Monero Deterministic Filter: Ring Repetition
Ring Repetition
| Case |
|---|
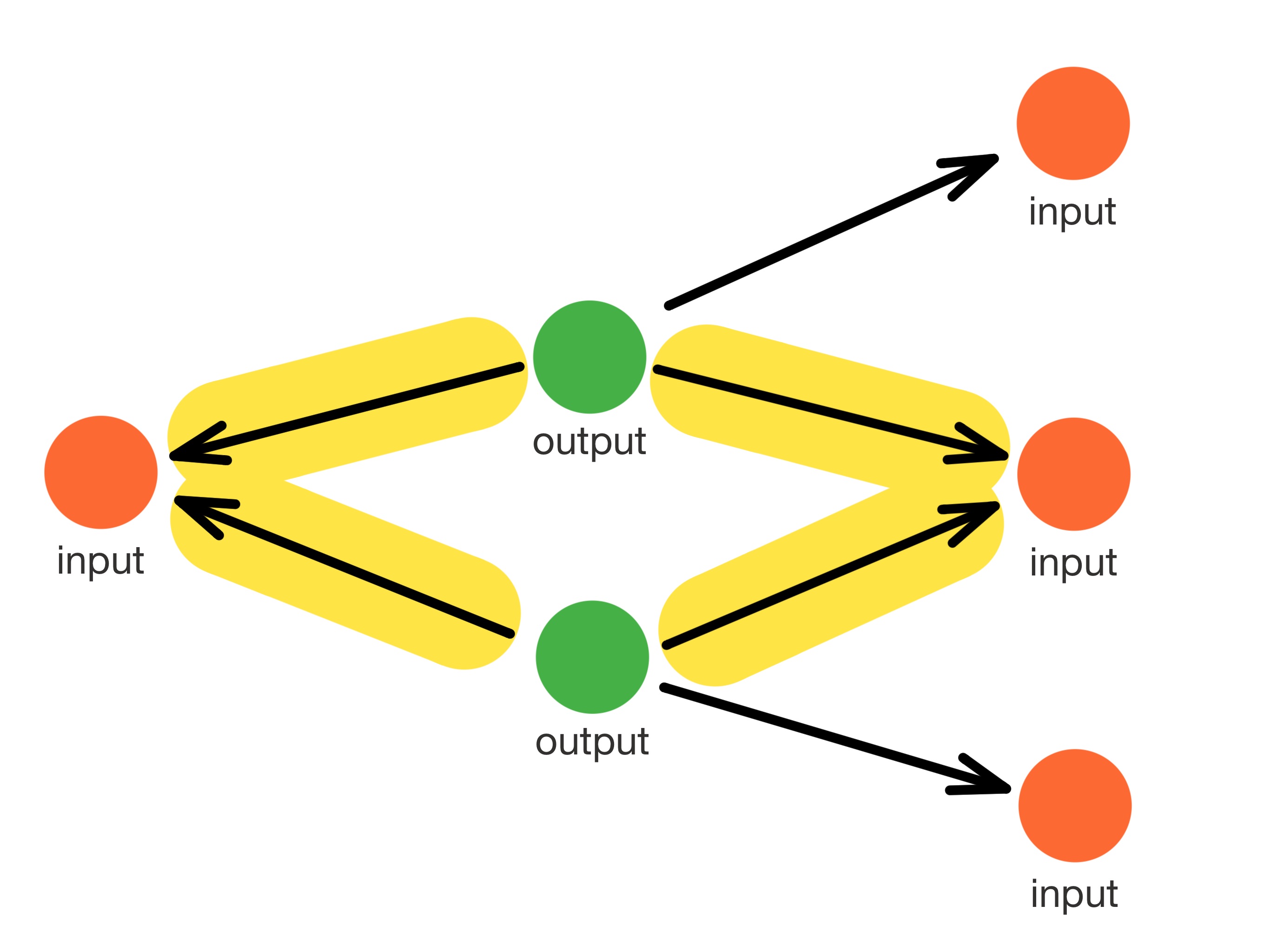 |
| Typical situation without any filters applied yet |
| Apply filter |
|---|
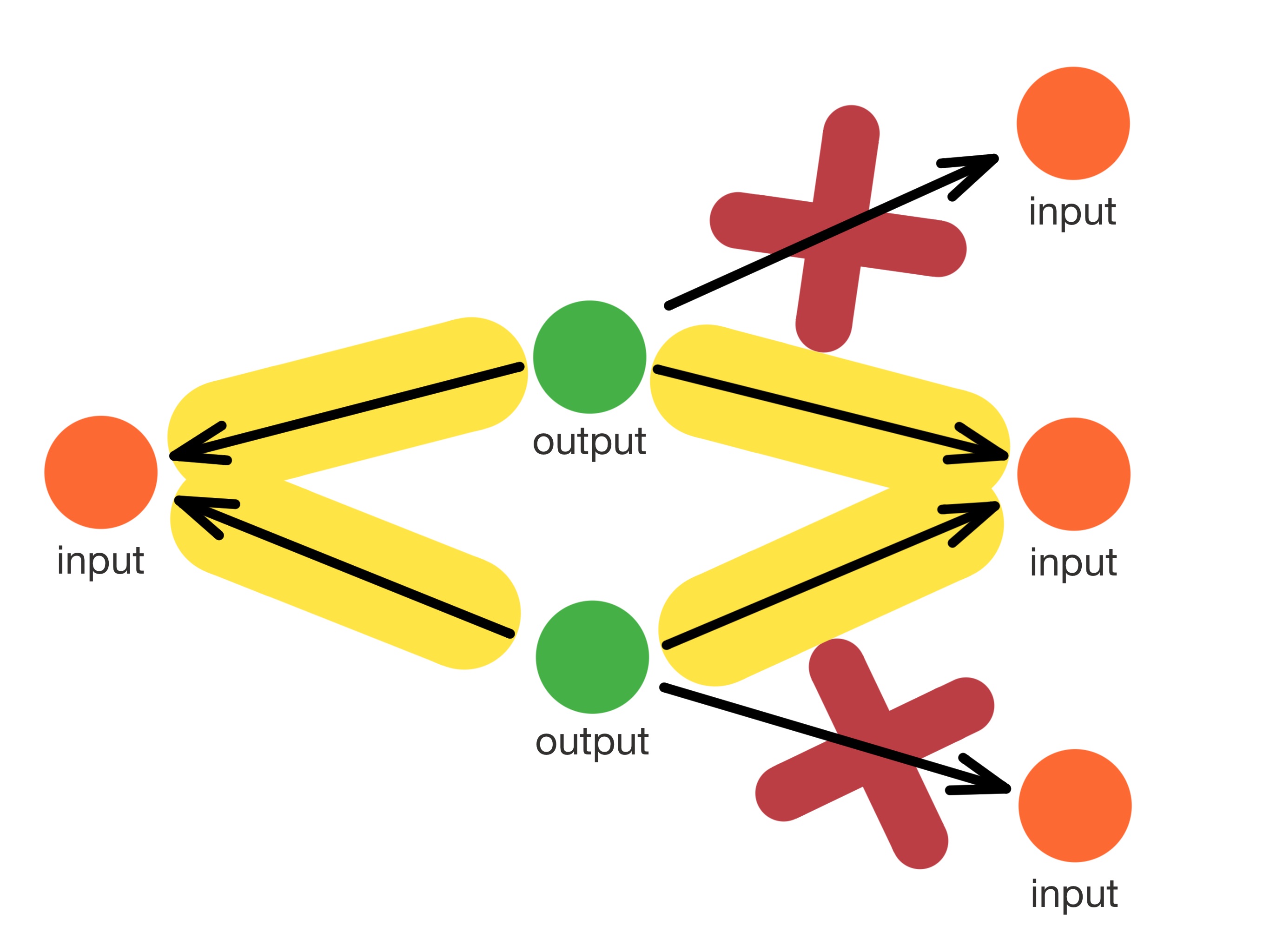 |
| The so-called ring repetition method uses multiple appearances of the same ring to identify spent outputs. This method simply identifies a collection of n separate n-rings containing the same outputs, where we can conclude that the ring is spent. This analysis was initially presented as semi-cooperative attack, where an adversary generates ring repetitions of controlled outputs to signal to other adversarial users that the ring is spent. See this paper |